Encryption and strong
passwords are important
for protecting your privacy

Encryption and strong passwords are important for protecting your privacy
The most common mistakes when using passwords and how you can avoid them.
- Using passwords with a personal reference, e.g. birth dates, family names, hobbies - attackers can find out these personal details, e.g. with research in social media, and thus attack your accounts.
- Too simple passwords, e.g. simple words - with so-called dictionary attacks, which can try through a lot of known words very quickly, your password is guessed in no time.
- Even inserting special characters or numbers into known words does not protect - attackers know these tricks too, of course, and try typical combinations quickly.
- Changing passwords too often - many people tend to use simple passwords in these cases and vary them slightly each time they change.
- Storing passwords in the browser or simply always staying logged in - if you ever leave your computer unattended in cafes, for example, or if it is even stolen from you, attackers who get to your computer may quickly be in your important accounts.
- Using the same password for several or even all accounts - if one of your accounts is compromised, in this case all other accounts are quickly at risk as well.
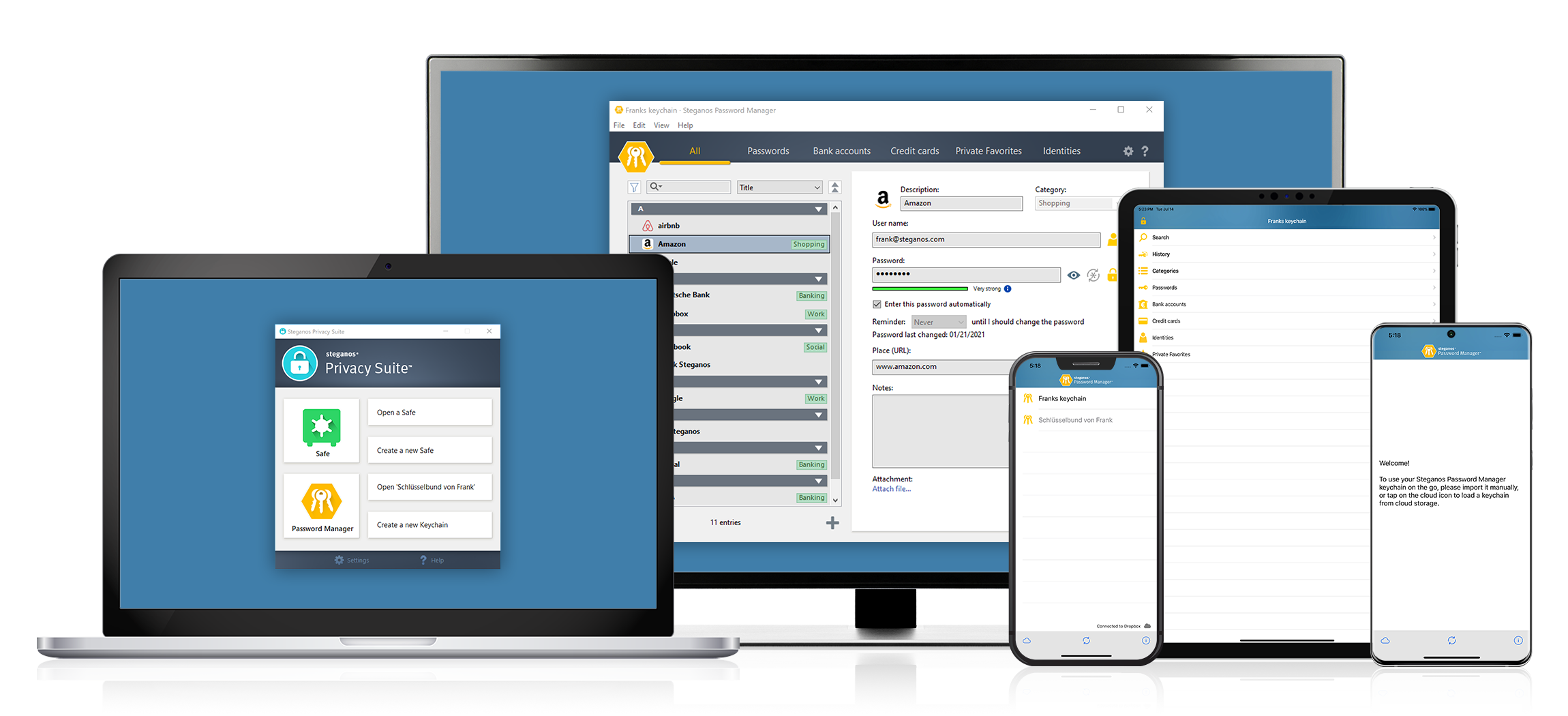
A great help to avoid these problems are so-called password managers, such as in Steganos Privacy Suite. With these, you can create a secure database of your passwords, secured by a single, strong password that you remember.
Passwords are only requested when needed and cannot be easily used without active action on your part on your PC. Since you only need to remember one password and the password manager creates strong, complex passwords for each account at the touch of a button, you avoid the typical mistakes and can also quickly replace compromised passwords with a new, strong password if needed.
Your passwords will also be safe in case your PC is lost, because without the secure master password that only you know, no one can access your password database.
In addition to using a password manager, it is recommended to enable and use secure two-factor authentication where possible, as this is yet another security factor that attackers will have to overcome even if your password is guessed or hacked in some way.
It is also a good idea to regularly check your PC for malware, because if your PC is compromised by Trojans or something similar, unfortunately even the best password won't help.
Encryption is a hot topic due to remote work, but just as important to protect your private and family data
At the latest since the introduction of privacy laws and regulations, data protection has become an important topic and since the significant increase of working remotely, the topic of data encryption has become an international trend, especially in companies. In this context, the importance of encryption in cloud storage is also increasing and, according to current studies, this will continue to grow in the future.
So far, the following data has been encrypted the most:
- personal customer data
- employee and personnel data
- corporate and financial data
- healthcare data
- billing and payment data
- intellectual property, such as patent, source code, and product data
- Family photos and documents
Encryption of company data
Data is playing an increasingly important role in everyday business and work. Especially sensitive personal data, but also data of business partners, customers or patients. All of these have a right to have their data treated with absolute confidentiality and stored securely in encrypted form. Internal and external documents must remain confidential, especially when they are stored and stocked.
This applies to data on the local computer, but also to data on servers and in the cloud.
Encryption of external data carriers
Data protection in the private environment has become increasingly important. At the latest since the increase in home office work due to the Corona crisis, attacks by hackers and data spies on private computers have increased dramatically. The number of cases of cybercrime registered by the police, especially in the private sphere, has risen continuously and has increased drastically, especially in the years of the Corona crisis.
That's why you should secure your personal data on USB sticks and external hard drives not only professionally but also privately.
Fit for the future with encryption
The digitalization of our society, private life and in the public authorities as well as corporate environment is constantly increasing, especially due to the clearly visible deficits in the Corona crisis. In addition to the technical development of the systems with which we work in everyday life, topics such as artificial intelligence or virtual realities are being added. As a result, the amount of digital data is increasing permanently.
For these reasons, the providers of encryption solutions are not standing still, but are constantly working on updates to ensure the highest standards of encryption and data protection in conjunction with a good user experience and easy-to-use technology. The Data Safe, which is part of the Steganos Privacy Suite, offers just such an easy-to-use technology, for encrypting and securing your professional and private data.
Our recommendation

 Highly secure encryption: the encryption algorithm safely stores all login data with AES 256-bit encryption
Highly secure encryption: the encryption algorithm safely stores all login data with AES 256-bit encryption
 Stores login data, credit cards and much more, and creates secure passwords for everything
Stores login data, credit cards and much more, and creates secure passwords for everything
 Includes free Steganos Password Manager apps for iOS & Android
Includes free Steganos Password Manager apps for iOS & Android
 AES-XEX encryption with 384 bits (IEEE P1619) with NI-hardware acceleration for optimal protection against thieves, snoops and intelligence services
AES-XEX encryption with 384 bits (IEEE P1619) with NI-hardware acceleration for optimal protection against thieves, snoops and intelligence services
 Create safes up to 2 TB (2.048 GB) in size
Create safes up to 2 TB (2.048 GB) in size
 Supports data encryption in Dropbox, Microsoft OneDrive, Google Drive and MagentaCLOUD
Supports data encryption in Dropbox, Microsoft OneDrive, Google Drive and MagentaCLOUD
How to keep data
safe from hackers
on vacation

How to keep data safe from hackers on vacation
When on vacation, people are often careless and not so attentive when it comes to cybersecurity. But there are ways to successfully protect yourself from data theft, and you don't have to be an IT professional to do it.
Who doesn't know how it is to check their emails or account balance while traveling. It's easy nowadays thanks to a wide range of smartphone apps. And since you don’t incur any unnecessary costs abroad, you’re more than happy to use the free Wi-Fi in the hotel, restaurant or cafe.
For many people, access to the Internet via a free hotel Wi-Fi is now an important criterion, or even essential, when choosing a vacation destination.
When you move into your room, one of the first things you do is set up and activate the hotel Wi-Fi. This usually goes quickly, select the correct network and you are already in the World Wide Web, this often without being asked to enter a password. The correct network is often recognized by its name, such as the name of the hotel, but names like "Guest" are also common. And since you are already looking forward to the pool or the beach, you don’t have much time to check the name of the access point careful enough.
Unfortunately, cybercriminals are aware of this very fact. For them, it is enough to set up their own hotspot in the neighborhood of the hotel, with a comprehensible name for the unsuspecting hotel guest. From then on, everything is easy for the criminals, from logging into email and social media accounts to passwords for online banking, they can now easily track, store and use everything for abuse.
Hotel servers are often hacked
But this approach is also popular at airports, restaurants and cafes. Unfortunately, in hotels, cybersecurity is often a stepchild that is neglected, there are several examples in which even at well-known hotel chains their hotel software and servers were hacked and customer data, credit card numbers, etc. were captured.
It is therefore no surprise that hotels are disproportionately affected by such cyber attacks.
Recommendations for better vacation data security
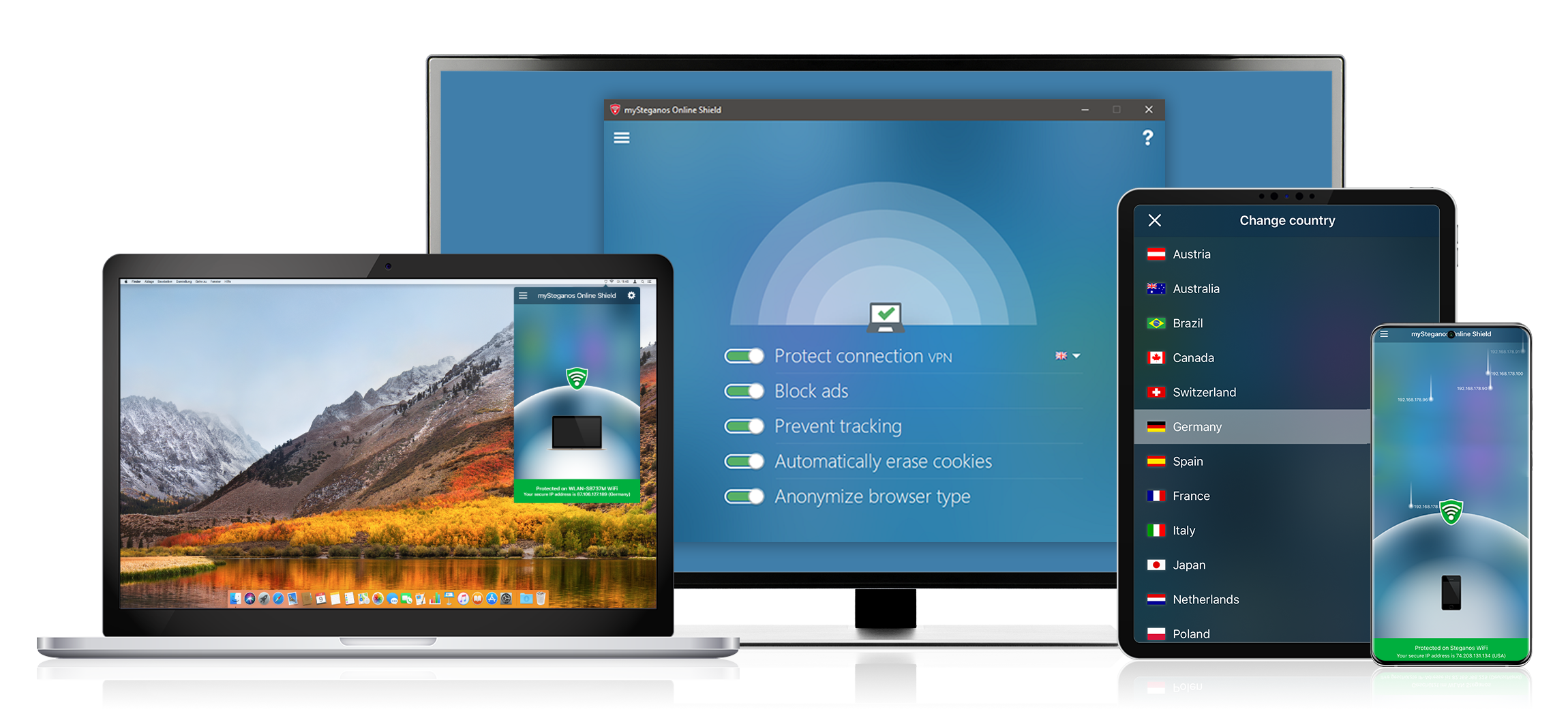
Thereby, there are simple and effective measures against the theft of your data by pretend hotel Wi-Fi. First of all, check carefully whether you have really selected the correct, official Wi-Fi of the hotel and use online banking best via a mobile connection (roaming), especially within the EU this is no longer an immense cost factor as in the past.
If you absolutely want to use online banking or access other security- and data-critical apps during your trip, such as email, online shopping or social media applications, you are well advised to install and set up VPN software at home before you leave.
VPN stands for "Virtual Private Network". Virtual Private Network means simplified: Your Internet connection is established via a server of the VPN service - comparable to a virtual tunnel - to the website you are visiting. The data transmitted from your computer or smartphone to the target server is sent through the established VPN tunnel to the VPN endpoint of the VPN provider. There, the data packets are anonymized and forwarded to the destination server.
Our recommendation
VPN software such as Steganos VPN Online Shield disguises your Internet connection, encrypts it and thus makes you invisible to hackers.

 Absolute security and privacy
Absolute security and privacy
 For all your devices - IT Security made in Germany
For all your devices - IT Security made in Germany
 Encrypted and private into the net
Encrypted and private into the net
 Use the internet as it should be
Use the internet as it should be
 Surf anonymously and without limits - disguise your identity and access blocked content
Surf anonymously and without limits - disguise your identity and access blocked content
 Protected from hackers worldwide - surf securely and anonymously in public WLAN hotspots
Protected from hackers worldwide - surf securely and anonymously in public WLAN hotspots
What is geoblocking and
how you can get around it

Simply bypass geoblocking
Surely it has happened to you before: when surfing the Internet you want to use a foreign service. But then, after a short time, a message appears: "This website is not available in your country".
Of course, such a message is annoying, as it denies you access to media libraries or other services such as news sites, flight bookings or online stores.
In order not to be stopped by such Internet blocks again and again, we would like to show you how you can easily bypass geoblocking.
Why does geoblocking exist at all?
Geoblocking is the geographical blocking of Internet content.
Geoblocking is used to deny access to Internet sites, for example, because streaming providers do not have the license for a certain country. Media libraries of the major TV channels but also Netflix and YouTube use geoblocking.
However, there is often geoblocking without you noticing it while surfing. For example, if you visit a foreign website of an online store, many companies will automatically redirect you to the domestic website. You can observe this by the domain extension, which for example changes from .com to .mx. This ensures that you can not benefit from foreign prices or special offers abroad.
How does geoblocking work?
When you open a certain web page, the server recognizes page where you come from. This recognition is based on the IP address, which is unique for each Internet user. It indicates in which country you live and which Internet provider you use. If the website is not allowed in your country or if the website owner does not want you to access the website from your country, you will be redirected to another website or a message will appear that the website cannot be accessed from your country.
The best solution against geoblocking is a VPN.
If you connect to a server in another country via VPN, such as the Steganos VPN Online Shield via the country selection within the VPN software, you can use its Internet connection and IP address. Corresponding websites, which would otherwise deny you access, then think you are in this country. This way you can outsmart the websites and their geoblocking and see content that was not originally intended for your country.
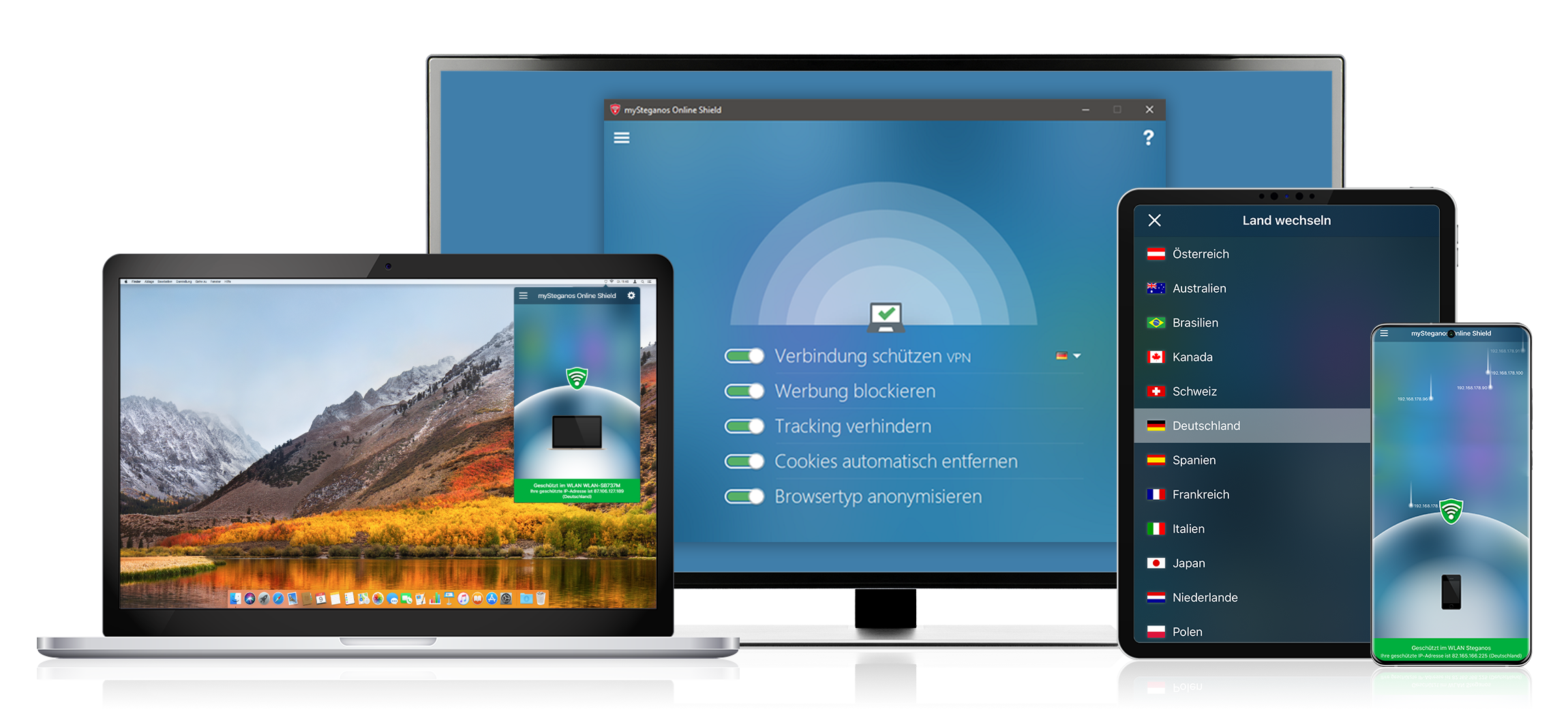
Bypass geoblocking with Steganos VPN Online Shield
Let's assume you are on vacation in Mexico and want to watch a show on the website of a well-known US TV channel on your laptop, tablet or smartphone.
You will see the following message

"Due to international rights agreements we only offer this video to viewers within the United States."

But luckily you have Steganos VPN Online Shield installed
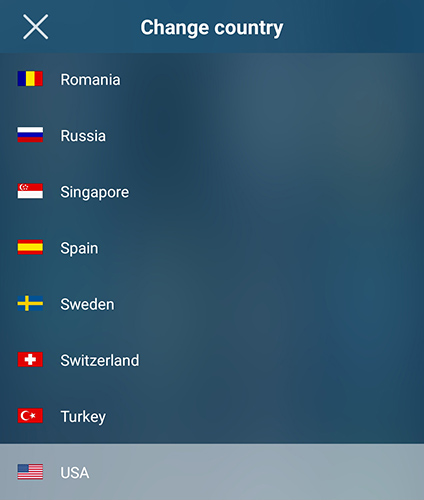
You open your Steganos VPN Online Shield, select the country selection in the menu and thus switch to servers located in the USA.
After that you load again the page of the desired TV channel or its media library and nicely you can watch your desired program.

Now you can watch your desired program

With Steganos VPN Online Shield you benefit from additional features:
- Surf securely, privately and anonymously, no matter where you are.
- Access foreign websites at home without being prevented from doing so by geo-blockers
- Be able to use your national websites abroad, such as the livestream of your favorite local TV channels
- Protect yourself in public WiFi from hackers and data spies
- Easily switch to a server in another country at any time
Fortunately, nowadays, using a VPN service is easy for everyone to apply without any prior technical knowledge. Whether you're on vacation, want to watch your popular season of a series already available abroad in your home country, or are a business traveler traveling to countries that block social media services or other sites. VPN offers the right and secure solution for every occasion.

 Absolute security and privacy
Absolute security and privacy
 For all your devices - IT Security made in Germany
For all your devices - IT Security made in Germany
 Encrypted and private into the net
Encrypted and private into the net
 Use the internet as it should be
Use the internet as it should be
 Surf anonymously and without limits - disguise your identity and access blocked content
Surf anonymously and without limits - disguise your identity and access blocked content
 Protected from hackers worldwide - surf securely and anonymously in public WLAN hotspots
Protected from hackers worldwide - surf securely and anonymously in public WLAN hotspots
How to bypass censorship on the Internet with a VPN
- A VPN establishes an encrypted tunnel to a secured server abroad.
- This allows you to bypass geoblocking or censorship at your current location.
- For example, you can access via VPN:
- blocked social media services (Twitter, Facebook, Instagram, TikTok ...)
- blocked news sites
- unavailable YouTube videos
- unavailable communication services (Skype, WhatsApp)
- blocked Google services
- other blocked websites - In addition, the VPN ensures that you are anonymous while traveling and no one can track what content you are accessing.>
When you use a VPN client such as Steganos VPN Online Shield, a secure, encrypted connection is established to a secured VPN server abroad.
If this tunnel is active, all your internet traffic will be routed through it, allowing you to bypass blocks implemented by your country or internet provider on the one hand, but also blocks implemented by the site you want to access, if applicable.
By encrypting, redirecting abroad and using your own DNS service, you bypass blocks in your own country, e.g. websites and services that are not allowed or censored in your current location.
Disguising your IP address and location, in turn, allows you to access websites and services that do not allow access from your current location, for example, for censorship reasons. Examples would be blocked videos on YouTube or various US news sites that are no longer accessible from the EU due to the GDPR, or even social media services and news sites that have been censored and blocked in one country.
To bypass blocking using a VPN service, all you need to do is install the VPN program you want, establish a secure connection with a server in a country where the website or service you want to use is available, and then use your apps or browser normally. It is recommended to additionally use a separate browser and block tracking as well as cookies as much as possible, as they can sometimes be used to determine your real location.
Our recommendation

 Absolute security and privacy
Absolute security and privacy
 For all your devices - IT Security made in Germany
For all your devices - IT Security made in Germany
 Encrypted and private into the net
Encrypted and private into the net
 Use the internet as it should be
Use the internet as it should be
 Surf anonymously and without limits - disguise your identity and access blocked content
Surf anonymously and without limits - disguise your identity and access blocked content
 Protected from hackers worldwide - surf securely and anonymously in public WLAN hotspots
Protected from hackers worldwide - surf securely and anonymously in public WLAN hotspots
Steganos VPN Online Shield $29.95 instead of $49.99 (5 devices / 1 year) & 64GB USB-Stick as a gift

Why the Recycle Bin is not enough
to securely delete your data

Why you should securely delete data and how Steganos Shredder helps you to do so
Moving files to the recycle bin and deleting them via the normal Windows method does not actually remove them from your physical disk. Only the references to where the data is located on the disk are removed. With appropriate software, it is easily possible to recover files deleted in this way, as long as they have not yet been overwritten.
It is therefore recommended to securely delete sensitive files and especially those that you copy to Steganos Data Safe when they are no longer needed. After all, the best encryption is of no use if the original data can still be read from the unencrypted area of your drives using relatively simple methods.
Below we explain how you can use Shredder to safely remove data from your drives. Steganos Shredder overwrites the deleted files with random data so that they cannot be easily recovered.
Securely delete files and folders with Steganos Shredder
-
First, open Steganos Data Safe and click on the Shredder icon.
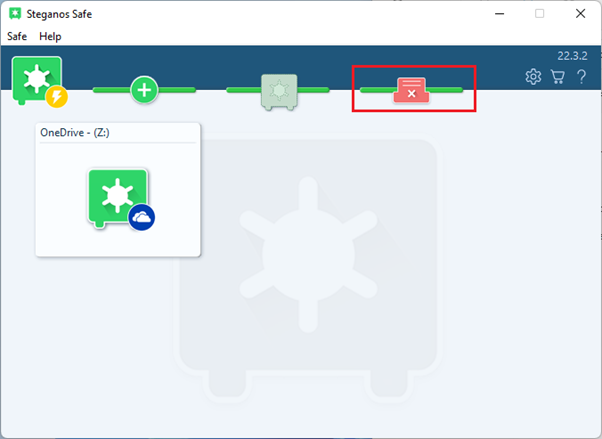
-
Then click "Add File" or "Add Folder" and select the files or folders you want to permanently delete. You can also simply drag and drop the files/folders into the Shredder window.
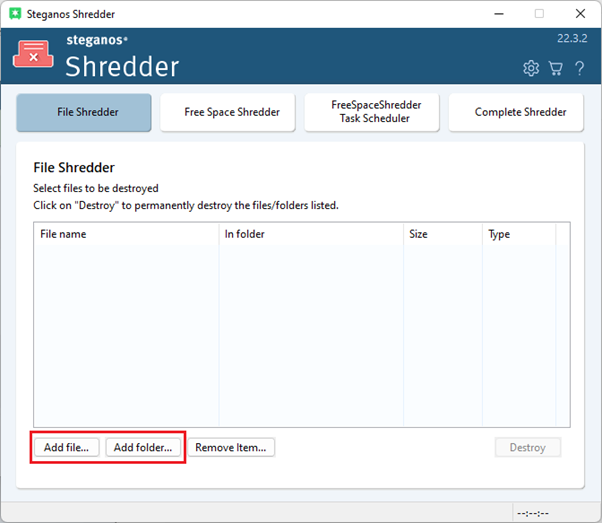
-
Once you have selected all the files you want to delete, click on "Destroy" and then on "OK". Before you delete files with the shredder, you should of course make absolutely sure that you no longer need them!
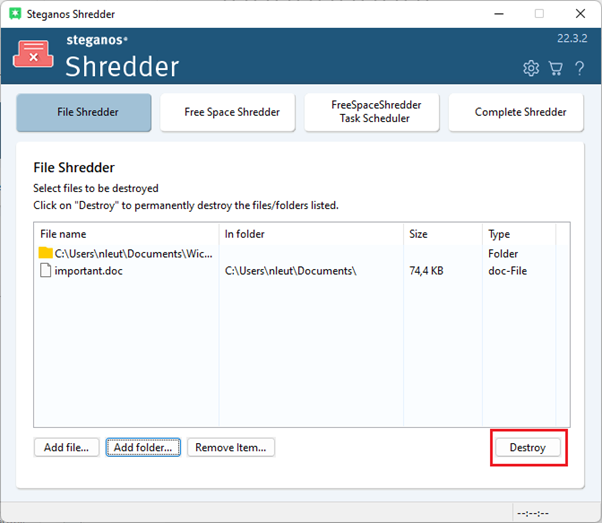
-
Afterwards, the files will be securely deleted and overwritten and cannot be easily recovered now.
Securely delete files that have already been deleted in the normal way with the Free Space Shredder
The Free Space Shredder is used when you have already deleted files via the normal way, but now also want to make sure that they cannot be recovered.
-
To use it, simply click on "Free Space Shredder" in the main overview of Steganos Shredder. The program will request administrator rights, please confirm them.
-
You will then see the main overview of the Free Space Shredder. Here, simply select the drive whose empty space is to be safely overwritten and click "Start". The process may take some time, depending on how much free space needs to be overwritten.
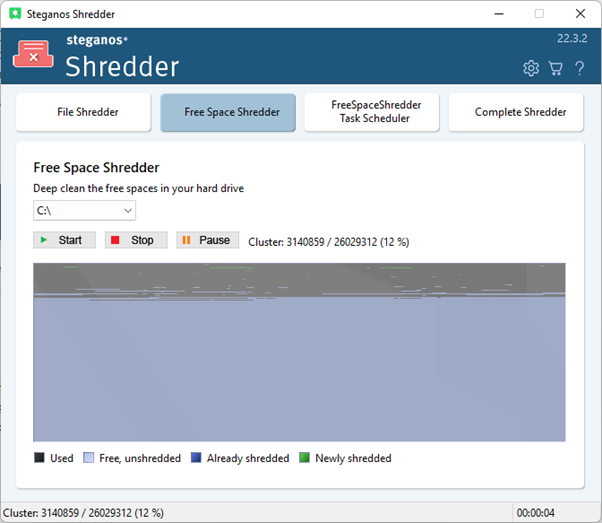
-
Once this process is complete, even files that you did not securely delete directly with the shredder can no longer be recovered.
Here you can learn more about Steganos Privacy Suite and Steganos Data Safe and how they protect your privacy. Both products have the described Steganos Data Shredder as a component.

